Menu
When it comes to threat hunting, you can’t just throw your net out and see what you catch. You need a starting point - something specific you can look for that is most likely connected to or will lead you to a threat. We refer to these as hunt hypotheses; an educated guess, based on past experience, a breach report, the MITRE ATT&CK framework, or any other lead you may have that helps you figure out where to start and what to look for.
Some things are harder to look for than others. The Pyramid of Pain (see below) illustrates how difficult it is to identify certain indicators to prove a threat hypothesis. The bottom of the pyramid represents things that are easy to look for and identify, like known bad hash values, IP addresses, and domain names. These are things that when you see them, you know you’ve found a threat. The higher up you go, however, the harder it is. The top of the pyramid is really where your threat hunting program needs to focus. It’s where an arsenal of solid hunt hypotheses will help you systematically uncover some of the most obscure attack tactics - and build your proficiency.
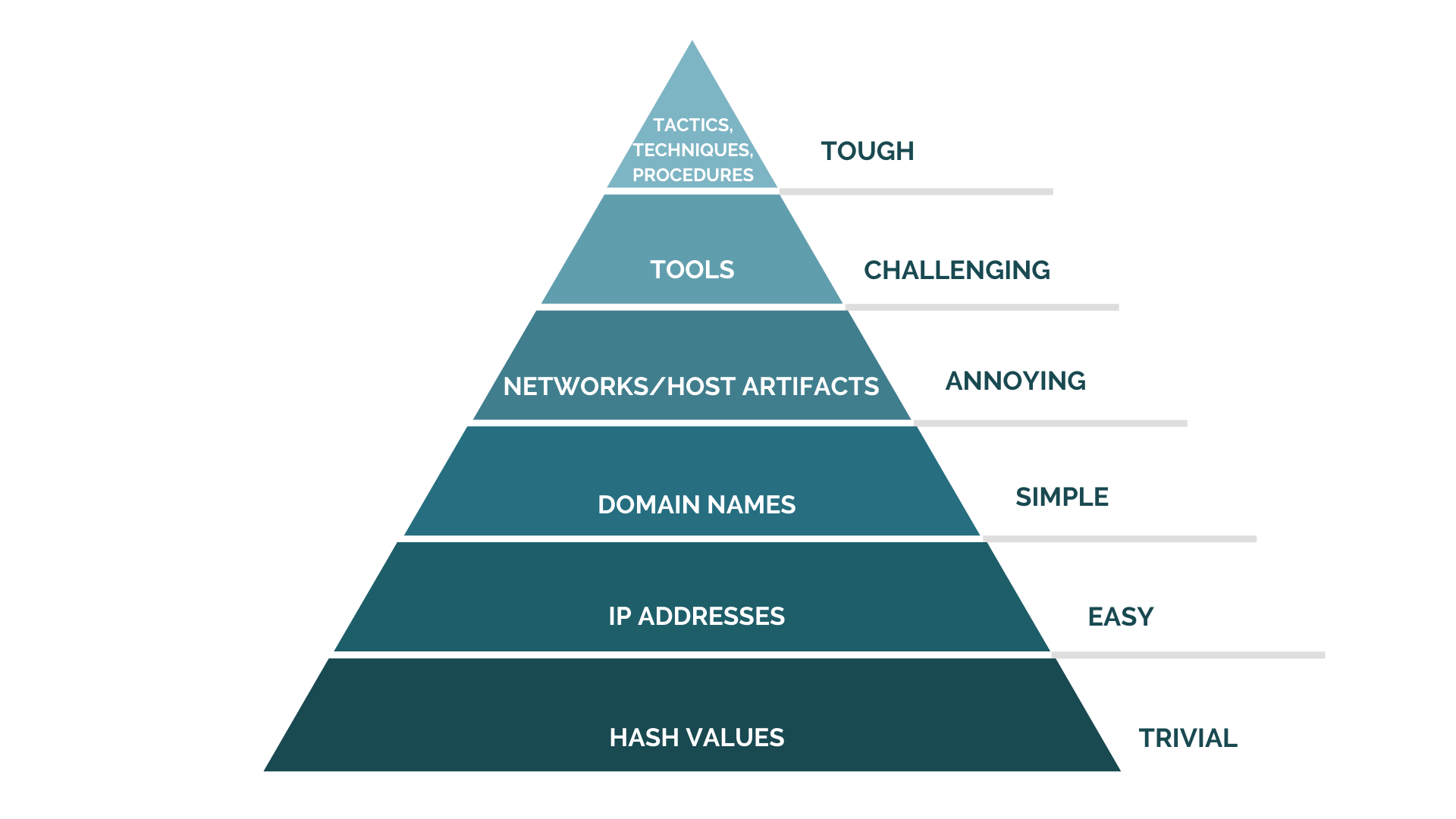
The more hypotheses you have, the more you can look for, and the more you can potentially find.
Having an arsenal of hunt hypotheses is but one of the elements critical to your team's ability to effectively track down attackers in your environment. Learn about the others - and how you can attain them - in our newly published ebook: "The 5 Elements of an Effective Threat Hunting Program."