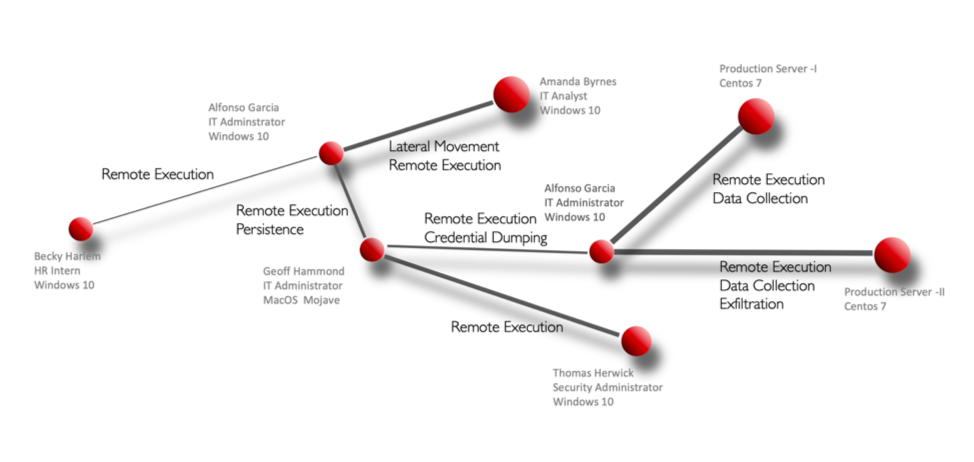
China has emerged as a major actor and its capabilities are only second to that of the United States based on NCPI 2020 Most Comprehensive Cyber Powers. The primary motive of the actor we evaluated seemed to be economic espionage, but ransomware and other activities were also observed in specific campaigns. The campaign we reenacted used a collection of malware tools that were both publicly available and proprietary in order to accomplish their mission.
Key TTPs used by the Chinese campaign
The attack uses spear phishing for initial access and then moves around using a variety of techniques. The attacker also used a variety of malicious software including rootkits, keyloggers, credential dumpers and backdoors to accomplish their goals. The malware beaconed out using multiple channels including DNS channels and DGA domains.
Below is an attack reenacted with key TTP’s associated with this group.
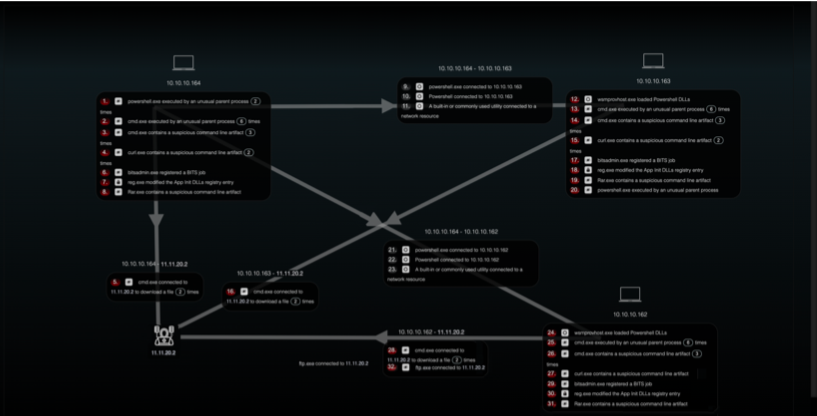
Here is the capture of the reenactment which includes 3 devices in the 10.10.10/24 network and the C2 server hosted at 11.11.20.2. The attack starts from 10.10.10.164, a compromised device and uses PowerShell remoting to remotely execute and move to 10.10.10.163 and 10.10.10.162. Interesting files were collected and RAR archives created before sending the compressed archives out using the file transfer protocol.
Iran is 23rd on the NCPI 2020 Most Comprehensive Cyber Powers but, over the past decade, has been developing a strong cyber offensive and information control programs. The primary motive of the Iranian actor we evaluated seemed to be surveillance of individual targets a well as telecom and airline sectors within the Middle East region. This group used malware with a backdoor functionality to log keystrokes, screen captures, audio recording, webcam captures, etc. to closely monitor activities of various individuals.
Key TTPs used by the Iranian campaign
The attack used spear phishing and compromised web servers for initial access and then moved around using remote desktop protocol, secure shell, etc. They also used a variety of publicly available malicious software and custom tools to accomplish their goals. The malware beaconed out using multiple channels including DNS and HTTP channels.
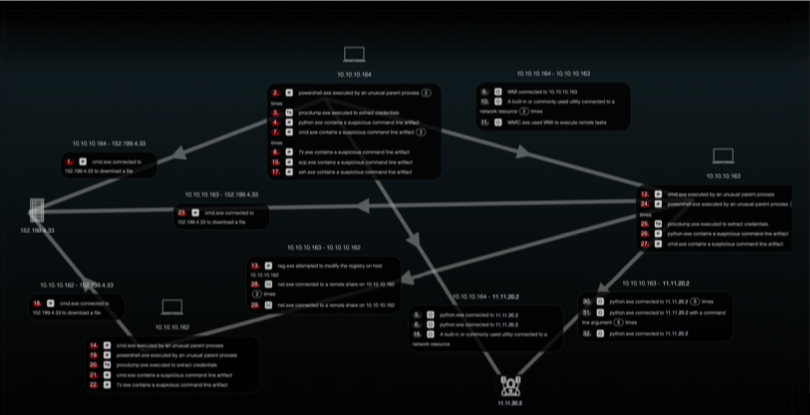
Above is an attack reenacted with key TTP’s associated with this group. The figure captures the enactment which includes three devices in the 10.10.10/24 network and the C2 server hosted at 11.11.20.2. The attack starts from 10.10.10.164, a compromised device, dumping credentials using ProcDump downloaded from Microsoft website, performing various reconnaissance activities, etc. and uses RDP protocol remoting to propagate to 10.10.10.163 and 10.10.10.162. Interesting files were collected and 7-zip archives created before sending the compressed archives for sending data back.
Russia is a major actor and is ranked 4th in the NCPI 2020 Most Comprehensive Cyber Powers behind US, China and UK. The primary motive of the Russian actor we evaluated seemed to be political in nature and targeted U.S government and infrastructure entities as well as political groups, universities and corporations with the intent of information theft. This group used a collection of publicly available and proprietary malware tools as well as operating system tools to achieve their goals.
Key TTPs used by the Russian campaign
Below is an attack reenacted with key TTP’s associated with this group.
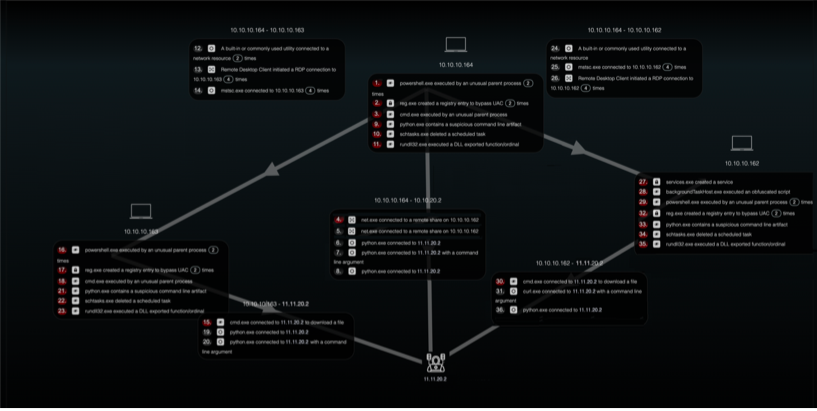
Similar to enacting the previous scenarios, we have enacted key TTPs within the 10.10.10/24 network and the C2 server hosted at 11.11.20.2. The attack starts from 10.10.10.164, a compromised device, persisting the malware using startup folder and scheduled tasks, executing python scripts to do network reconnaissance and communicate with C2 server, dumping credentials, etc. The campaign uses Remote Desktop Protocol clients to propagate to 10.10.10.163 and 10.10.10.162. Interesting files were collected and 7-zip archives created before sending the compressed archives for sending data back.
In all of these campaigns, actors enter the environment via social engineering, compromised credentials and exploiting vulnerabilities in external facing servers. Given that humans tend to make mistakes and that software always has some unidentified vulnerability, it’s difficult to plug all defenses in order to prevent an attacker from getting in. However, once an attacker gets in, we observed a number of commonalities from a TTP perspective including how they move laterally within the environment, deploy persistent malware, dump credentials, escalate privileges, communicate with C2 domains, love off the land, etc. Most of these techniques are dictated by what the operating systems allow. As a result, the core of a campaign is more predictable than it’s beginning and end. If we need to detect and thwart these campaigns, we should cast a wide net for this vulnerable and predictable core of the campaign as at some point every campaign will employ some of these TTPs to accomplish their goals.
Given the volume of data that is being collected, it is hard to manually hunt down every activity that forms the core of these attacks. Instead, to fully understand these attacks, machines need to do the tracing and identifying of campaigns. In order for these machines to be successful in the hunting process, they need to understand the commonalities within the different attack types and then dynamically interrogate behaviors with AI that understands security. By collecting the evidence of attacker behavior from telemetry sources at machine speed, security teams can easily see the complete attack campaigns.
Every attack campaign is unique and different. However, the central core of the campaigns are constrained by what’s feasible within the operating environment. This is the weakness we need to exploit, with the power of AI based interrogation, to identify the inner core of the campaign. Once this core is identified, it is easier to put together the missing pieces from start to finish. Understanding complete campaigns in real-time will equip the security teams with enough time to thwart the attacks before they inflict irreparable damage to the organization.